
As in previous example of ransomware attacks, cybercriminals usually go straight for the end users. There are times however, they take a less direct approach, as they did with an adware campaign that targeted Google Chrome users.
Copyfish is a translation plug-in for Google Chrome. By no means is it one of the most used Chrome extensions, but based on the most recent information from the Google's Web Store, it had somewhere over 30,000 users. To a criminal, that is a fairly large pool of potential victims.
You may not have heard of online ad fraud and clickjacking, but they're very widespread problems. It's difficult to know exactly how widespread, too, because they often go unreported.
On Friday, an unknown hacker hijacked the Copyfish Chrome extension from its original authors and pushed an update that inserted ads in people's web pages.
The hack took place because one of the Copyfish developers fell for a simple phishing trick and accessed a link in an email he thought he received from the Chrome team. In reality, the email came from the phisher and urged the Copyfish developer to update his extension, or it would be removed from the Chrome Web Store.
When the developer accessed the link, he was redirected to a copy of the Google account login page, where the developer then entered his credentials for the developer account.
The login page was hosted on chromedev.freshdesk.com, and surprisingly the extension's developer didn't think it was strange, even if Google has hosted its support desks on its own domains for more than a decade.
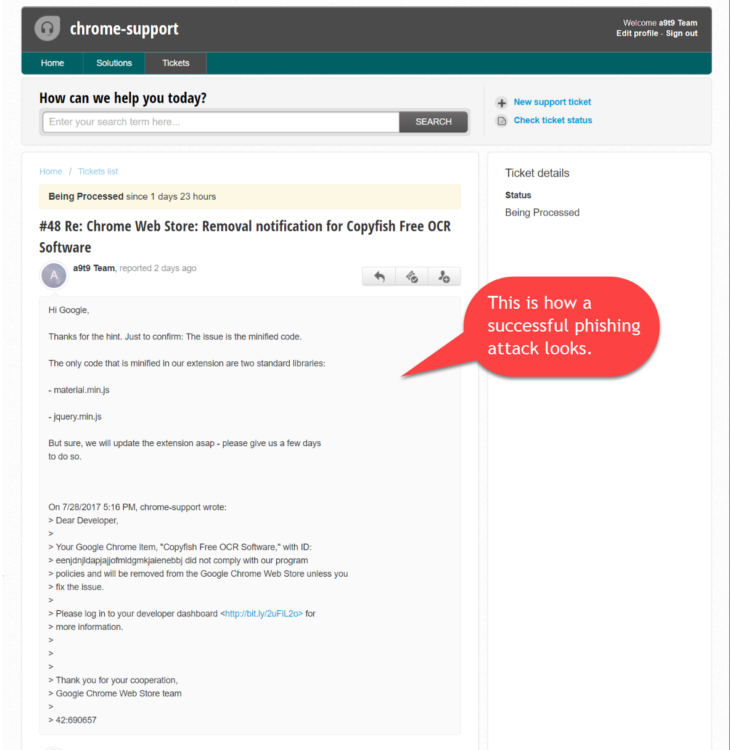
A day later, the hacker had pushed a malicious update (v2.8.5) for the Chrome Copyfish extension, which is a pretty powerful tool for extracting text from images and PDF files.
The update added extra JavaScript code that loaded ads on all the pages a user viewed. Despite this intrusive behavior, it took Copyfish developers a full day to realize what had happened.
Unfortunately, by that point, the hacker had transferred the extension to his own developer account, out of the reach of the original authors, who were desperately trying to reach a Google staffer to have the extension pulled down.
At the time of writing, the extension is still under the hijacker's control. Users are advised to remove it from their browsers. The Copyfish team says its Firefox add-on is safe and under their control.
QWERTY Concepts, an IT support provider based in New Jersey, always emphasizes on the risks that end users pose to company networks. Stanley Kaytovich, an IT director stated "Protection starts at the endpoint". "End users pose one of the biggest risks to a company security noawdays" he stated. QWERTY Concepts is a provider of IT services for businesses. "Security is always a top consideration for any implementation" he stated.









