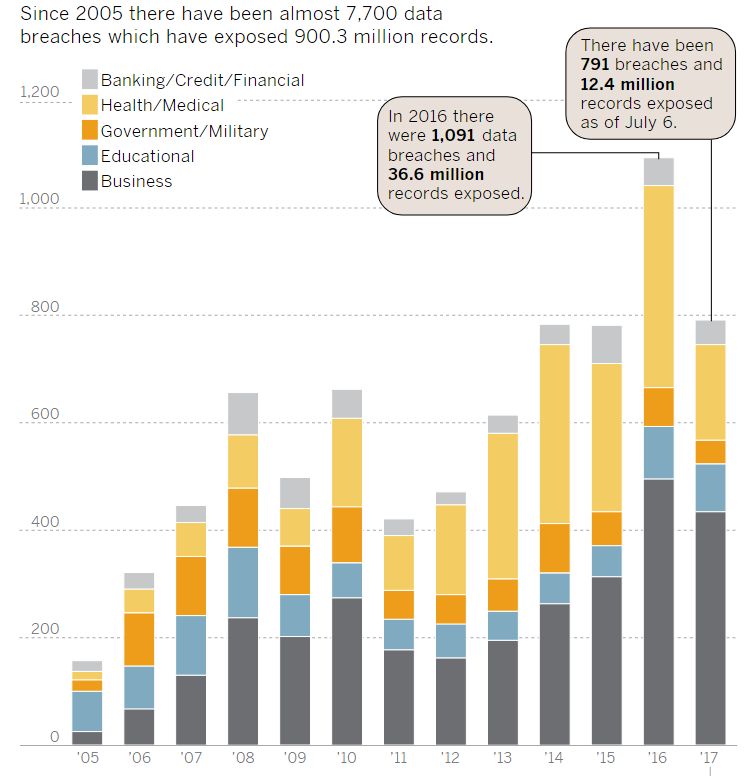
According to a report released by the Identity Theft Resource Center and CyberScout, data breaches are running 29% above last year. Hacking was the leading cause of data breaches nationwide, more than 790 so far this year.
Although two-thirds of data breach notifications or public notices did not report the number of records compromised, more than 12 million records have been exposed.
“Only 33 percent of data breaches reported this year have made the number of records exposed publicly available,” said Karen A. Barney, director of research and publications at Identity Theft Resource Center, an increase of 13 percent over 2016 mid-year numbers.
The resource center tracks breaches in the categories of financial, health care and medical, government and military, education and business.
More than half of all beaches this year have occurred in business, followed by health care and medical. Breaches in the medical and health-care industry are most likely to include the number of records involved. More than 80 percent of breaches in 2017 that were reported to Health & Human Services included the number of records.
According to the resource center, a data breach occurs when a name is released in connection with a Social Security number, driver’s license number, medical or financial record. The exposure is tracked when it occurs because of a phishing or hacking attack, theft, negligence or error.
“Exposure of the Social Security number is the primary trigger across the board for a state data breach notification,” Barney said.
Exposure that includes a user name or email address in combination with a password or security information that would allow access to an online account may also trigger a notification in California, the first state to enact a data security breach notification law.
This year, personal information has been compromised by the unauthorized acquisition of data at universities, businesses, banks, medical and government institutions:
Major breaches involving the exposure of names and other information have also occurred this year:
Since 2005, there have been almost 7,700 data breaches which have exposed more than 900 million records in the U.S. according to the resource center.









